Confirmed Breach Identify Attack Vector In Logs

Threat Intelligence Everything You Need To Know Recorded Future

Application Protection Report 2019 Episode 4 Access Attack Trends In 2018
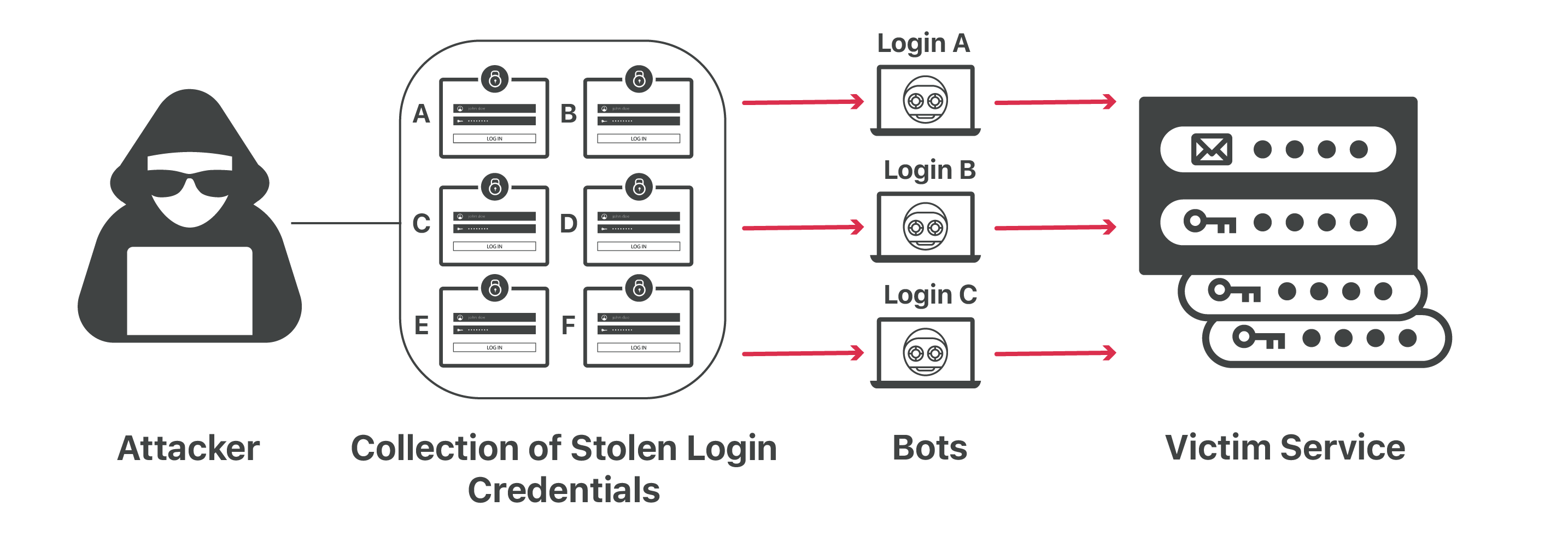
What Is Credential Stuffing Credential Stuffing Vs Brute Force Attacks Cloudflare
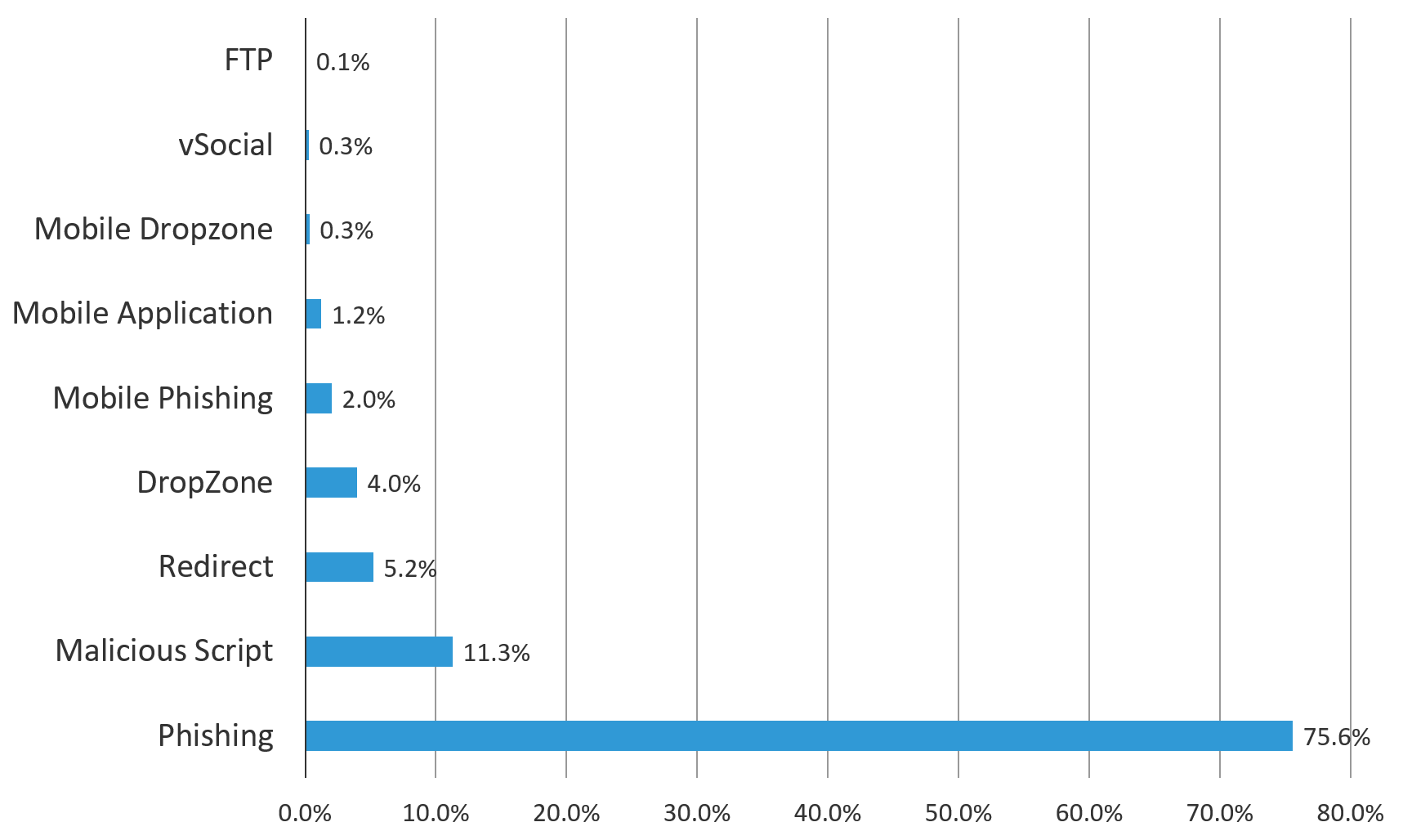
2018 Phishing And Fraud Report Attacks Peak During The Holidays
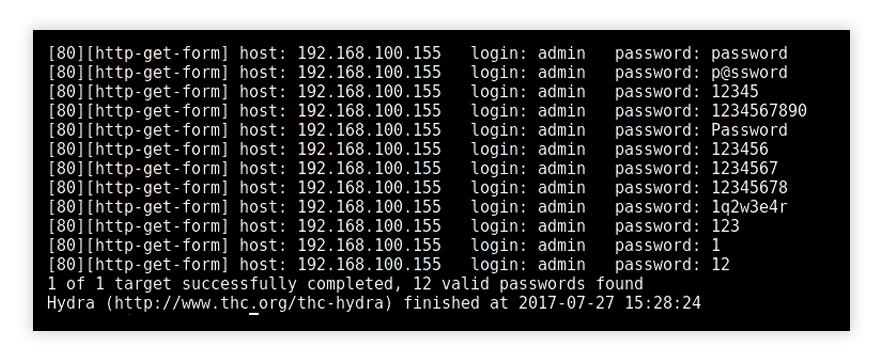
What Is A Brute Force Common Tools Attack Prevention Imperva

Enisa Threat Landscape Report 2016

Page 5 Sonicwall

Threat Intelligence Everything You Need To Know Recorded Future

Meltdown Security Vulnerability Wikipedia

Application Protection Report 2019 Episode 4 Access Attack Trends In 2018

New Centrify Survey Too Much Privilege Not Enough Pam Powered By Zero Trust Centrify
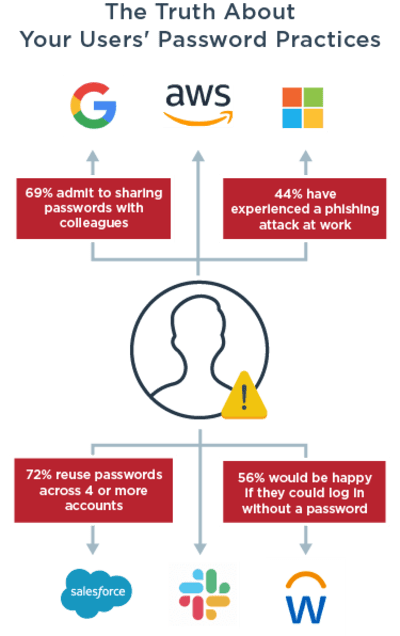
What Is Multi Factor Authentication Mfa
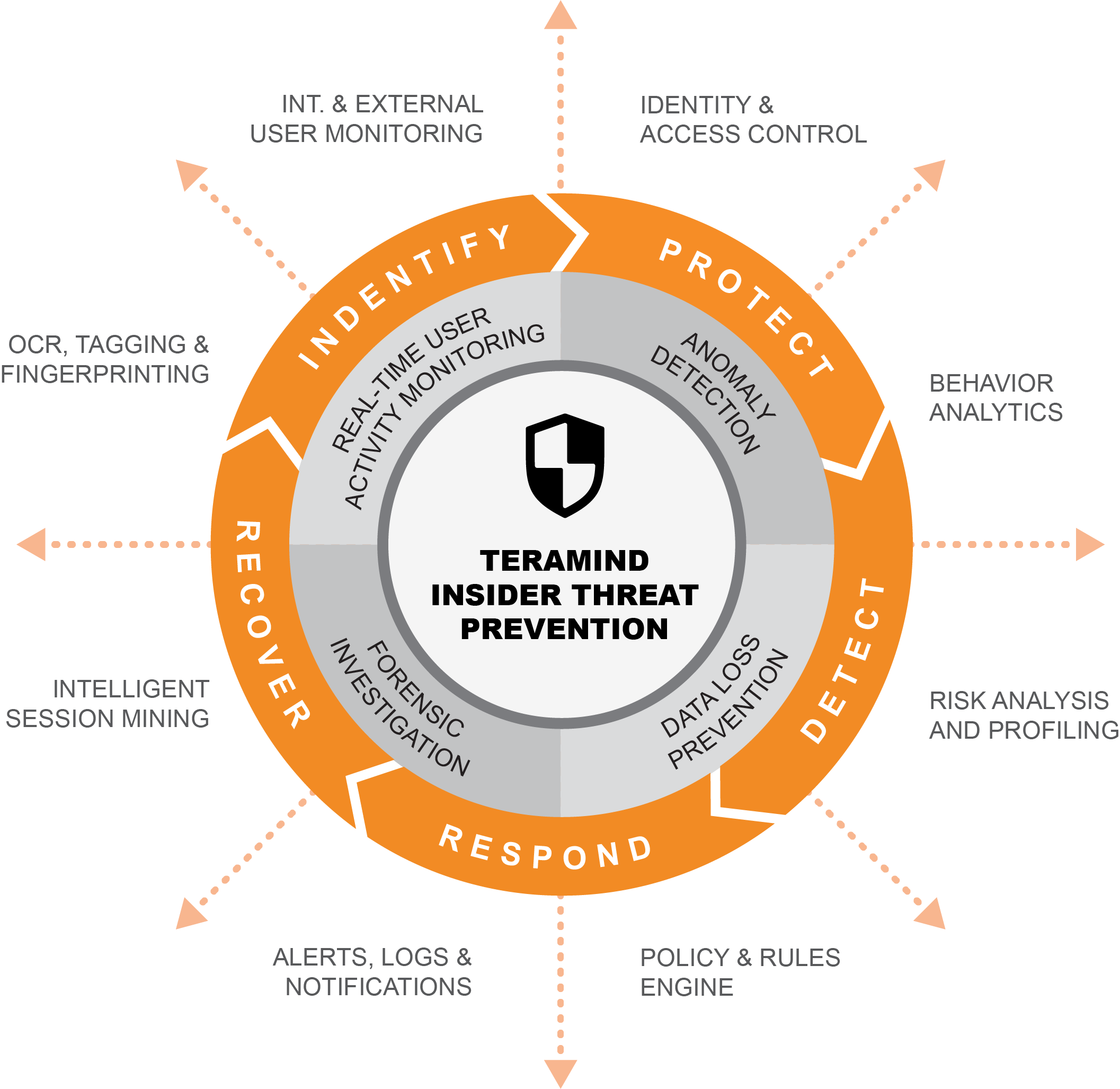
Insider Threat Monitoring Detection Prevention Teramind

Monitoring Data Breaches
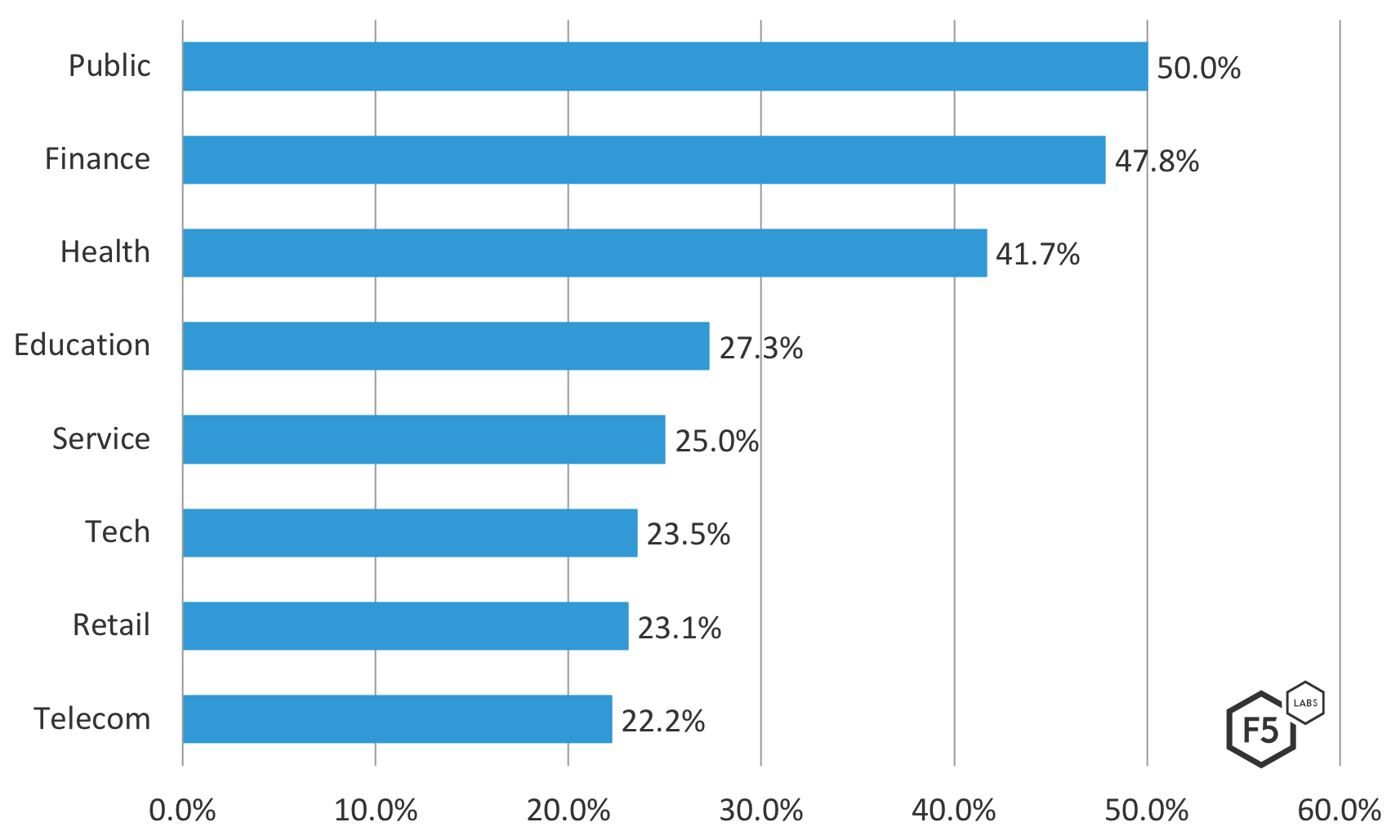
Application Protection Report 2019 Episode 4 Access Attack Trends In 2018
Aws Iam Enumeration 2 0 Bypassing Cloudtrail Logging Rhino Security Labs
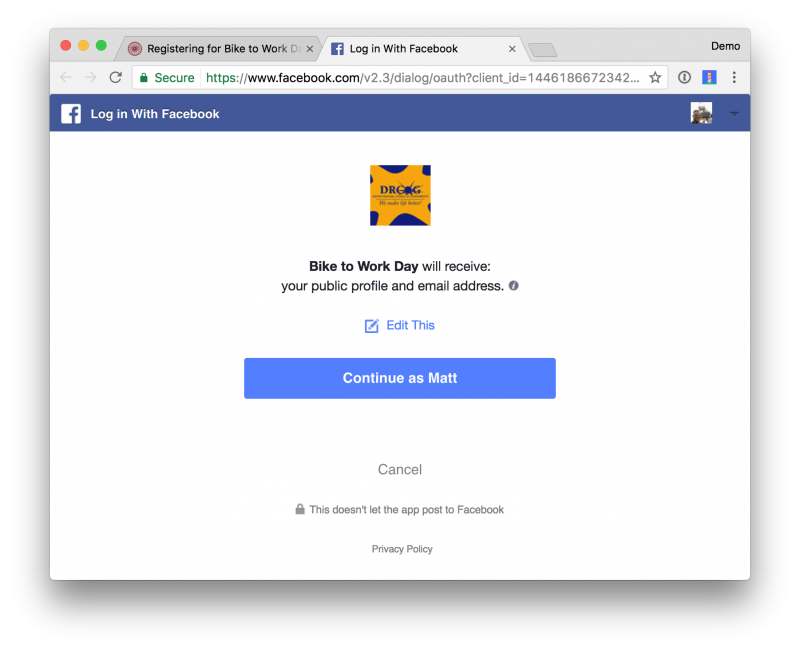
Microsoft Warns On Oauth Attacks Against Cloud App Users Threatpost

Application Protection Report 2019 Episode 4 Access Attack Trends In 2018

Explore Our Active Directory Security Solutions Alsid

Phishing Attack Prevention How To Identify Avoid Phishing Scams In 2019 Digital Guardian